DANTECTF and wellcome my new crypto teammate
-------------------------------------------------------------------------
Introduce my self
Im kon-chan, a ctf player UwU
Im insterested in all category UwU
------------------------------------------------------------------------
This is some solution of me, so lazy to writeup but hope guys love it
-Web
-> Unknow Site 1
->Unknow Site 2
->Dante barber shop
->Dump Admin
-Misc
-> HellJail
LET'S GO
Unknow Site 1
Look at it
And yeah, it was there.
Fisrt flag was easy hehe.
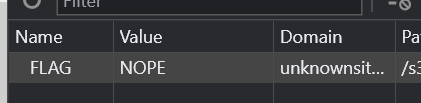
Unknow Site 2:
just now we saw in robots.txt there are some strange directories. Let's check them out. I found in /s3cretDirectory3/ there are many php files, one of them will hav flag
When i click on any file, it renders 'Hello There User!' and in the cookie there is a key flag set value of NOPE
Dante Barber Shop
going back to the index, and reading the source, i noticed that the img tags are all numbered from 2-7
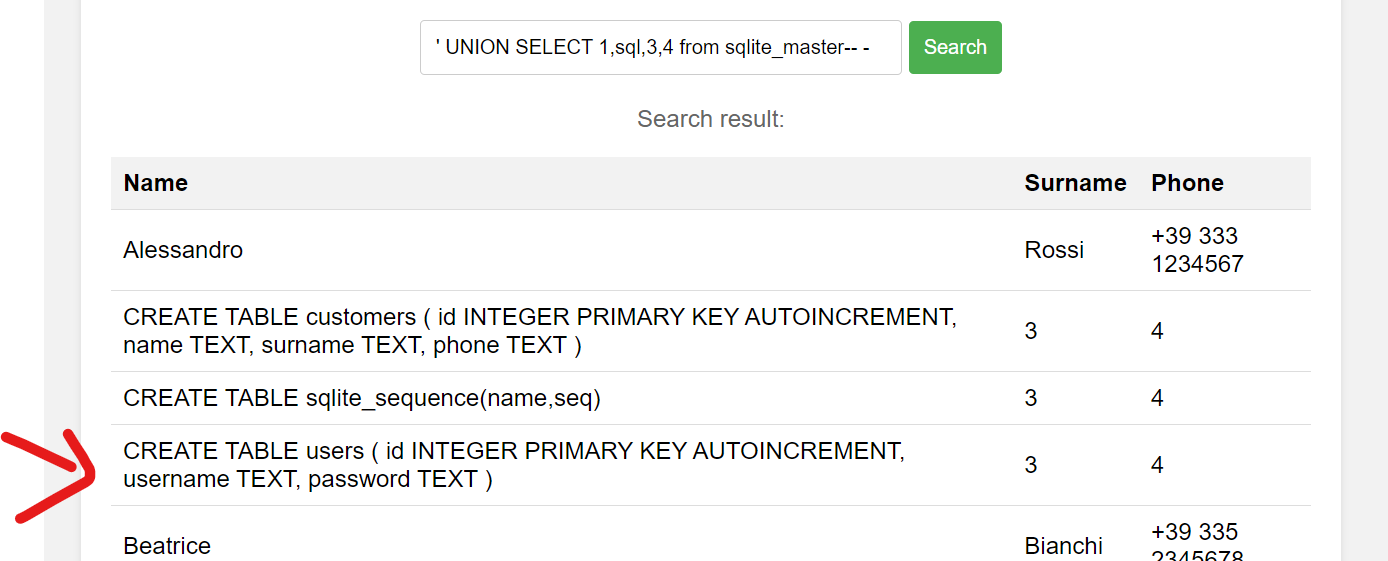
After login, I noticed that it looks like sqli, I love this vuln :D
Try ' to check. It bring back many infomation
Backend use sqlite so i read sqlite_master :D. But fisrt check number of columns
login as admin and received flag
Dumb Admin
Let's explore this site
i tried simple sqli payload: admin' or '1'='1'-- -
Logged in successfully
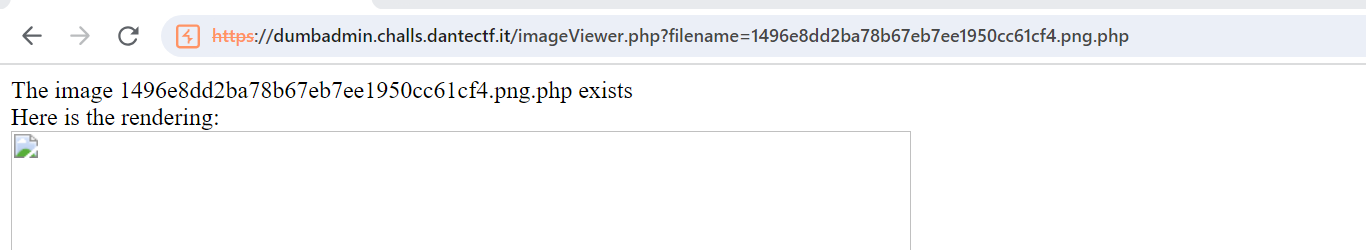
this was file upload, upload a shell to rce :V
btw, php extension didn't work. try .png.php and it worked
Nothing is here :(
read source code, u will see file located,
i got it
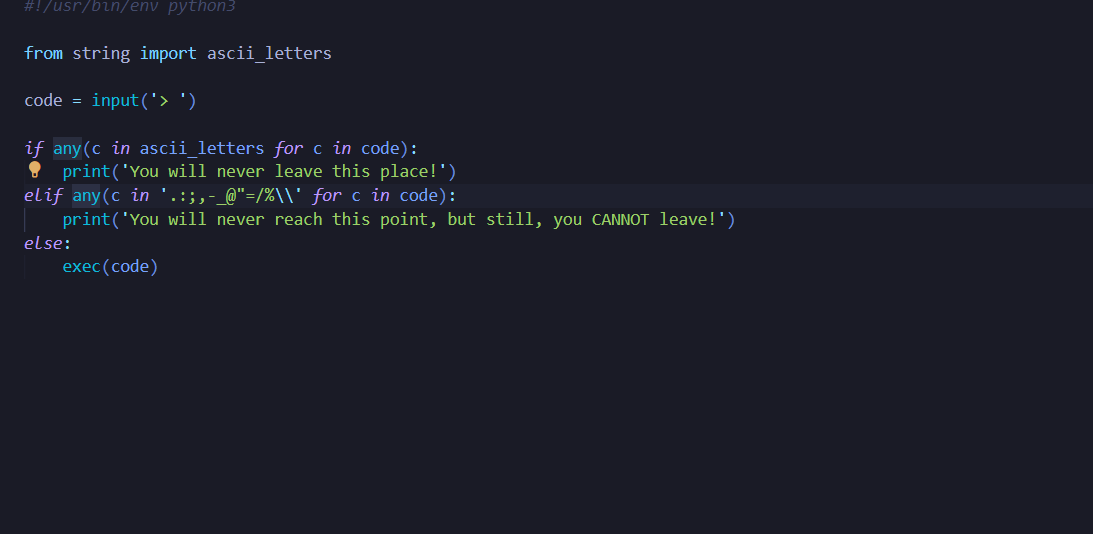
HellJail
the author gave me a source
sink is exec().
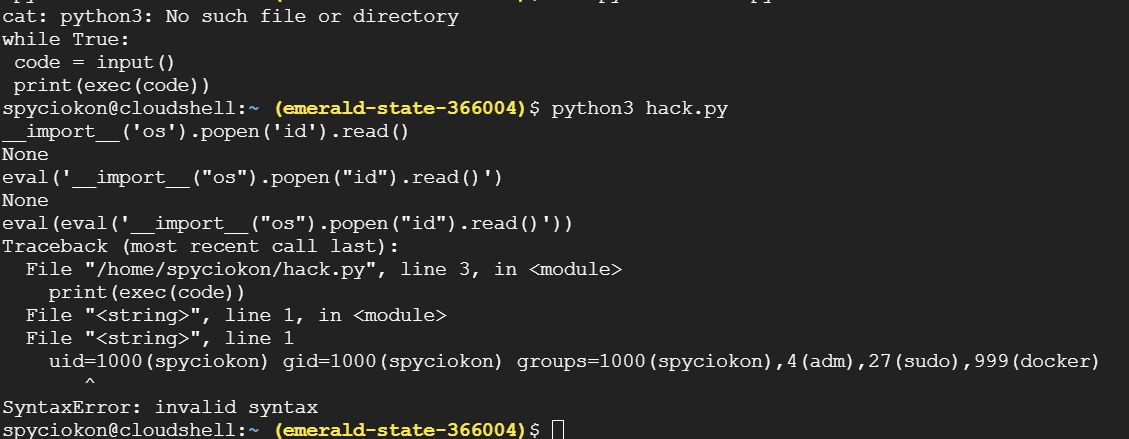
Let's debug :v
i cant use ascii_lettes.
My idea was use eval() to execute arbitrary command
:v
My payload contains forbidden characters however in python 3.x, allows you to use italized characters to write your expressions, which aren't ascii
Taking advantage of that we will bypass. However, importing os will cause an error.
No module named '𝘰𝘴'
We will take ord('o') and ord('s') then use chr() function and concatenate the characters via eval()
Similar to `_` and `.`
here is my code and payload


































Nhận xét
Đăng nhận xét